INTRODUCTION
The immune system is a distributed decentralized system that functions without any centralized control. The immune system has millions of cells that function somewhat independently and can detect and respond to pathogens with considerable speed and efficiency[1][2][3]. Lymph nodes are physical anatomical structures that allow the immune system to rapidly detect pathogens and mobilize cells to respond to it. Lymph nodes function as: 1) Information processing centres, and 2) Distributed detection and response network. We introduce biologically inspired computing that uses lymph nodes as inspiration. Lymph nodes process information. They facilitate detection of pathogens, process that information and help co-ordinate the output or response to infections. The immune system is a complex adaptive system that has evolved for millions of years under co-evolutionary pressure from pathogens. It has evolved mechanisms to efficiently detect and respond to pathogens. Innovations include lymph nodes which serve as information processing centres: they integrate signals from neighbouring tissues, process it, match pathogens with immune system cells and then send out cells to respond to the pathogen. A schematic of this is shown in Fig. 1. Only a few cells (1 in a million) of the immune system can recognize a specific pathogen[1]. Once a particular immune system cell detects a pathogen, it must replicate and build copies of itself and then act against the pathogen. Additionally, detection and the response to pathogens must be rapid otherwise the pathogen will be able to replicate and kill the host organism. Lymph nodes serve to facilitate the serendipitous encounter of rare immune system cells with their antigen. Response against the pathogen is complicated by two considerations of body size of the animal (the size of the system): 1. Certain cells of the immune system release chemicals called antibodies which are further diluted in blood. Hence in larger animals, antibodies get diluted more in the larger volume of blood. Hence larger animals must secrete more absolute quantities of antibodies[1]. 2. Certain cells of the immune system physically search for infected cells. This search is more difficult in larger animals since the search is through a larger physical space[4][6].
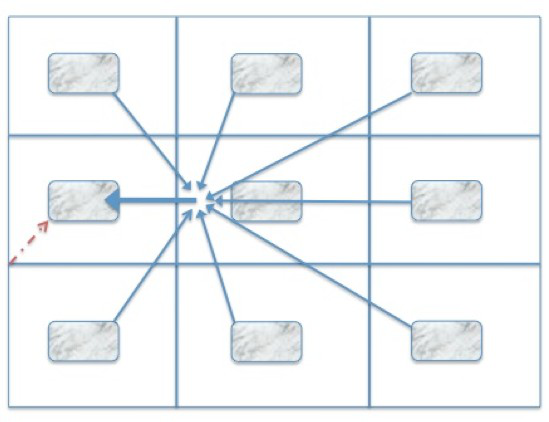
We can draw valuable inspiration from how the immune system has designed a distributed detection and response infrastructure. The hardware of the immune system (lymph nodes)[1] has co-evolved with its software (T-cell recirculation and search strategies)[4][6] to enable the immune system to mount effective and timely responses to pathogens. Here we outline applications to diverse human-engineered complex systems like social networks, intrusion detection in distributed systems, cluster allocation in distributed systems of computers and mobile robots. We argue that the biological immune system can provide powerful metaphors and inspiration for distributed computing in human-engineered complex systems like clusters of computers, peer-to-peer networks and online social networks. Lymph node inspired techniques can also complement and provide a powerful context in which to situate other immune system inspired techniques like negative selection[7], clonal selection[8] and dendritic cell algorithms[9]. In the following sections, we outline some biological preliminaries and the general principles of lymph node inspired computing. We lay out applications to human-engineered systems, fault-tolerant distributed computing, computer security and other resource constrained distributed systems.
BIOLOGICAL PRELIMINARIES
The draining region of a lymph node is the region of tissue adjoining a lymph node. Dendritic cells patrolling the draining region home to the nearest lymph node to present antigen. Cells of the immune system called dendritic cells search for pathogens in tissue and once they find it, home to lymph nodes. Within lymph nodes they present antigen to other specialized immune system cells called T-cells and B-cells. Almost 1 in a million T-cells and B-cells are able to recognize this antigen[1]. Once the antigen is recognized, T-cells exit the lymph node and home to tissues to find infected cells. B-cells go through a similar process and secrete chemicals called antibodies that neutralize pathogens. Previous work has shown that there needs to be a balance between the local time of detection of pathogen with global time for response against the infection (by secreting antibodies)[1][2][3]. The optimal architecture of lymph nodes needs to be sub-modular in order to ensure that the time to detect and respond does not scale appreciably with the size of the system (in this case the body size of the animal). Each lymph node has a protection (with one copy of each immune system cell specific to pathogens)[1]. This is a modular search unit which is iterated in larger animals. If cognate immune system cells are so rare, then how does the immune system detect pathogens quickly and mount an effective immune response? The answer lies in lymph nodes that are: 1. Modular, 2. Parallel, and 3. Privileged metabolism: The metabolic rate of lymph nodes is invariant with the size of the host animal[10].
APPLICATIONS TO FAULT-TOLERANT DISTRIBUTED COMPUTING AND SEARCH IN SOCIAL NETWORKS
MODULAR SEARCH IN DISTRIBUTED SYSTEMS OF COMPUTERS
Lymph node inspired computing can be applied to a system where controllers try to find computer clusters that can be used for computation. Let an artificial lymph node be composed of a number of clusters and a process queue that will manage requests to schedule programs on a cluster of computers[11]. Also let there be a number of such artificial lymph nodes that have the capability of communicating with each other. An artificial lymph node is a computer in charge of a number of clusters. This computer will store the process queue and also will have some memory and computing power to communicate with other artificial lymph nodes. We seek to minimize the total time to find a cluster. There is a trade-off between the local cost of traversing through the queue in a lymph node which is O(n2) and the global cost of communicating with other lymph nodes which is O(N / n) (here n is the number of clusters in a single lymph node and N is the total number of artificial lymph nodes in the complete system). We assume that the global cost of finding another cluster in another lymph node that can service some process requirement is proportional to the number of artificial lymph nodes (where N/n is the number of artificial lymph nodes in the system). Minimizing the total time cost, we get: n = O(N1/3) This implies that in larger systems, the number of clusters within a single lymph node should grow larger but only sub-linearly in the number of total clusters in the system. Hence a lymph node inspired approach would balance local costs of queue traversal and global costs of finding artificial lymph nodes with another cluster that can service the process[11].
IMMUNE SYSTEM INSPIRED DECENTRALIZED SEARCH IN SOCIAL NETWORKS
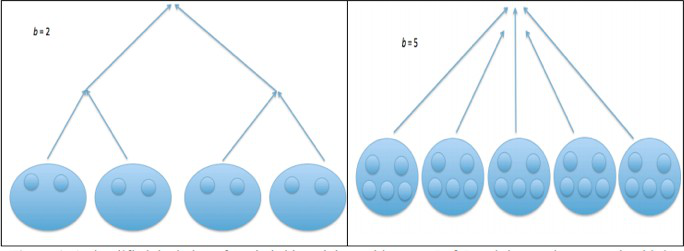
Social networks are characterized by short diameters and it is very easy to find another person within about 5 to 6 hops[12]. This is exemplified by experiments performed by Stanley Milgram where letters posted by complete strangers found their way to people across vast geographical distances[12]. Kleinberg[13] gave a very elegant explanation of this phenomenon based on the small-world degree connection of nodes in a network. The work implicitly ignored considerations of space, since long-distance links are assumed to have the same cost as short-distance links. Work in the immune system is motivated primarily by constraints of space. An infected site lymph node has to incur increasing communication costs in larger organisms, since it has to recruit immune system cells over larger physical distances (and hence long-distance links have higher associated costs). Real world social networks also densify i.e. the average number of neighbours that an individual has increases with time. Hence such networks will have a communication cost not only due to space but due to the requirement of maintaining a certain number of connections. In work inspired by conceptual similarities between a lymph node and a social community, a non-spatial communication cost was incorporated in order to introduce the realism of individuals communicating within communities[14]. It has been shown that the optimal strategy that minimizes the time to find someone using only local information is where the size of communities and the number of communities both increase with the size of the system. This is ultimately predicted to lead a speedup in search for information. Such a strategy would decrease the time required to search for rare information in online social networks[14]. An example lymph node inspired social network architecture is shown in Fig. 2.
APPLICATIONS TO COMPUTER SECURITY AND RESOURCE- CONSTRAINED DISTRIBUTED SYSTEMS
INTRUSION DETECTION SYSTEMS
Lymph node inspired strategies can be used to augment intrusion detection applications like LISYS[15] and process Homeostasis (pH)[16]. pH adaptively reduces computer processing speed to reduce the spread of malware. A lymph node inspired approach can be used to augment pH in the following manner: a subnet of computers would be an artificial draining region and a security node in charge of the subnet would be analogous to a lymph node. A lymph node inspired architecture can balance local communication (intrusion detection) and global communication (alert propagation). We note that in some cases it may not be advisable to spread alerts immediately in pH[16], since the performance of the whole system may degrade or false alerts can propagate rapidly throughout the system.
LOW POWER RESOURCE CONSTRAINED DISTRIBUTED SYSTEMS
A lymph node inspired approach may be particularly useful for security of low power distributed systems like mobile phones. Mobile phone viruses propagate by small hops to neighbouring within-range devices, and hence physical space and proximity of devices is important[17]. Since mobile phones are constrained to communicate to nearby neighbours (through Bluetooth connections and proximal cell towers), the lymph node analogy can be extended to view mobile phone transmission towers as artificial lymph nodes and the area of mobile phone users serviced by it as the draining region.
APPLICATION TO HUMAN-ENGINEERED SYSTEMS
MODULAR SEARCH IN MULTI-ROBOT SYSTEMS
Our work can also be applied to an immune system inspired robotics systems. The draining region of a lymph node can be patrolled by robots. The artificial lymph node is a central computer. Robots in the draining region communicate with the central computer (artificial lymph node). A lymph node inspired architecture can lead to speedup in search times for robots[1][2][3][4] by balancing the local time to find a solution (similar to a pathogen) and the global time to propagate it to other artificial lymph nodes.
SEARCH IN PEER-TO-PEER SYSTEMS
Distributed peer-to-peer systems are used to provide services like search and content integration. Computer nodes store data or service and no single node has complete g. lobal information. Decentralized search using local information is used to locate data. In this case, artificial lymph nodes would be clusters of computer nodes that store information. Artificial lymph nodes communicate with each other when they need to find information. Using a lymph node inspired can lead to speedup in time to search for information in peer-to-peer systems[3].
GENERAL PRINCIPLES OF LYMPH NODE INSPIRED COMPUTING
Here we outline the general principles of lymph node inspired computing. The immune system aims to balance the local time of detection of pathogens with the global time for response against pathogens.
BALANCE BETWEEN LOCAL DETECTION AND GLOBAL RESPONSE
The key argument is that response against pathogens by the immune system should minimize energy expenditure. This leads to a particular scaling of the size and number of lymph nodes: a relationship for how the size and number of lymph nodes should vary with the size of the animal[1]. We assume that energy spent is linear in the size of the organism, i.e. all organisms spend a constant fraction of their energy budget on the immune system. Similarly we strive to build systems that have approximately linear or poly-logarithmic scaling in terms of memory or computation requirements.
MISCELLANEOUS CONSIDERATIONS
Any distributed computer system with a client-server relationship will lead to different kinds of tradeoffs between local and global communication. Such systems could have a master- slave relationship in which individual components report aggregated data to a processing centre (local communication) and processing centres distribute data globally among all components (global communication)[1][3]. A lymph node inspired strategy can enhance message propagation times and increase robustness in such systems. The final optimal architecture will also depend on architecture of the system and the idiosyncrasies of the system; for example in certain intrusion detection systems like process Homeostasis[16] it may not be optimal to spread information globally (which would lead to performance degradation of the whole system) and hence the optimal strategy would be to contain all information locally.
GENERAL THEORY OF LYMPH NODE INSPIRED SEARCH AND RESPONSE IN DISTRIBUTED SYSTEMS
Generally, if the local and global communication costs scale with exponents α and β, we have the time to find information locally and then spread it globally as ttotal = O(n α ) + O(N γ / n β ) where n is the number of computers in an artificial lymph node and N is the number of artificial lymph nodes. Minimizing the expression with respect to N, and assuming a power- law scaling relation, we get the following general relation[11] for the number of nodes or computers within an artificial lymph node: n = O(N γ / (α+β) ) We also have the following regimes based on the relative values of the parameters: 1. If γ < α + β we have sub-linear scaling. 2. If γ > α + β we have super-linear scaling. 3. If γ = α + β we have linear scaling. 4. If γ/(α + β) = 0 we have no scaling (constant). 5. If γ/(α + β) < 0 we have negative scaling.
DISCUSSION
Lymph nodes are physical anatomical structures that allows the immune system to rapidly detect pathogens and mobilize cells to respond to it. Lymph nodes function as: 1. Information processing centres, and 2. Distributed detection and response networks. We introduce biologically inspired computing that uses lymph nodes as inspiration. This is shown schematically in Fig. 3.
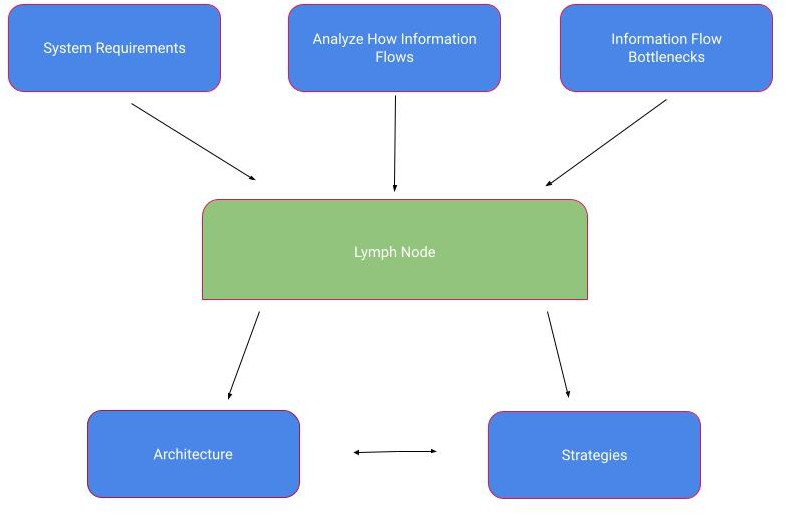
The immune system is able to and rare spatially localized pathogens and eliminate them in a timely manner. The immune system uses specialized cells to find pathogens in anatomical regions called lymph nodes. A sub-modular arrangement of lymph nodes could lead to fast elimination of pathogens in the immune system and also faster search for solutions in immune inspired distributed systems of computers[1][2][3][4][5]. Each lymph node has a modular unit of protection called a protection (that contains the 1 in a million immune system cells specific to a pathogen). This is a modular search unit that may be iterated in larger animals and allows the immune system to detect pathogens quickly and mount an effective immune response. Our approach highlights the tight coupling and co-evolution of hardware (lymph nodes) vs. software (algorithms for guiding T-cells to sites of infection) in complex biological systems like the immune system. The software would be specific algorithms or search processes that guide T-cells to infected cells in tissue. The hardware is the physical infrastructure of lymph nodes and circulatory networks. Both have co-evolved with each other to produce a system that is capable of detecting an event and responding to it efficiently. Human-engineered complex systems can draw valuable inspiration from such systems. The hardware of the immune system (lymph nodes)[1] has co-evolved with its software (T-cell recirculation and search strategies) to enable the immune system to mount effective and timely responses to pathogens. Here we have shown how these techniques can be applied to systems like mobile networks and outline applications to diverse human-engineered complex systems like social networks, intrusion detection in distributed systems, cluster allocation in distributed systems of computers and mobile robots. We argue that the biological immune system can provide powerful metaphors and inspiration for distributed computing in human-engineered complex systems like clusters of computers, peer-to-peer networks and online social networks. Such a lymph node inspired approach can also be applied to the Internet of Things. Lymph node inspired techniques can also complement and provide a powerful context in which to situate other immune system inspired techniques like negative selection[7], clonal selection[8] and dendritic cell algorithms[9]. These techniques can provide valuable inspiration for building systems that scale gracefully as we increase the size of the system. We hope that this would lead to immune system inspired computing that captures all the complexities and power of the immune system in human-engineered complex systems.
DECLARATIONS
1. Funding No funding was received for this work. 2. Conflicts of interests The author declares no competing interests. 3. Availability of data and material The study generates no data. 4. Code availability No code is used in this manuscript. 5. Authors’ contributions SB conceptualized and led the study and wrote the manuscript. 6. Ethics approval The study does not use animal or human data and no ethics approval was required. 7. Consent to participate The study does not use animal or human data and consent to participate was not required. 8. Consent for publication All authors gave consent for publication.
