INTRODUCTION
The basis of the implementation of the systems related to the storage, processing and transmission of information is the infocommunication infrastructure[1][2]. In the practical transmission of information, not only the absolutely necessary information is transmitted. Usually, additional information is displayed next to it. In public communication, the information is not always sent to a specific person or object. Therefore, the additional information can be obtained by anyone. In this way, the additional information facilitates the unsolicited acquisition of the information and later its use[3][4][5][6]. At the same time, the energy problem of handling information in practice also appears to have a connection with additional information. To model the energy consequences, the problem is approached from the point of the control theory, and the systems are examined according to their energy balance. The components used for modeling are defined on a philosophical basis for universal usability[7][8][9][10][11]. Thus, the modeling procedure is multidisciplinary and can be generally used in RDI[12][13][14][15][16][17] and education[18][19][20], and in legal regulations[21][22] each in its territory. This study presents the role of additional public information in the possibility of obtaining information and in the practical handling of information[23] through the example of an internet game. The Open Source Information Acquisition (OSINT) is one element of the social engineering information acquisition palette, among others[24]. The conscious planning of information management is also important due to its sensitive use. This design should include the energy requirement of handling additional information, and it should also limit the possibilities of intentionally reducing deduplication procedures, by taking into account unnecessary redundancy[1][2]. Based on the analysis of the game, the study also points out that the additional information can be a very significant part of the transmitted information set. This is, among other considerations, one of the major drivers of the growing energy demand of systems and of the big data effect
ADDITIONAL INFORMATION
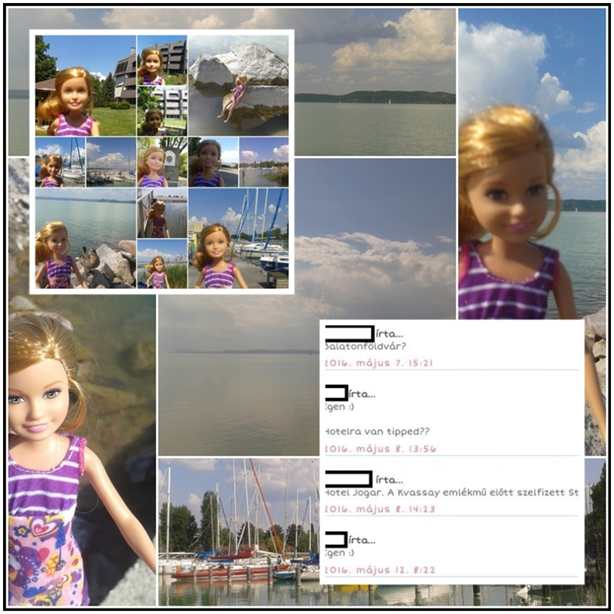
The communication can be formulated with the additional information on the receiving side: the additional information is the information that appears next to the content that is intended to be conveyed, and from a certain research aspect, it represents an added value[23]. Through the example of an older online game, it was shown that in addition to the intentionally disclosed information, the transmitted data carries additional information for the receiving party. More specifically, it showed an example of incorporating additional information and decoding it. The game proceeded as follows: based on the selfies made by toy dolls from different geographical locations, players had to guess where the dolls were[23]. A photo montage related to the game is shown in Figure 1. The evaluation of the game revealed that players were able to find the location within half an hour, usually based on the landscape and the construction details in the selfie’s background. But some additional information that had not originally been requested was also decoded: they were able to establish, among other things, the manufacturer of the dolls, the vintage or the originality of their clothing. They also provided information about the owner’s attachment to toys. Thus, it became certain that the additional information could be decoded from many more aspects than originally planned[23].
ENERGY MODEL
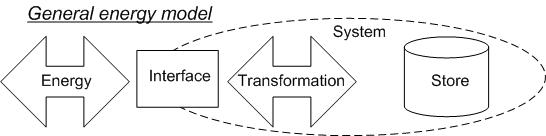
The additional information can be examined from several aspects. This is an examination of energy problems, and the amount of data is proportional to the energy required to deal with it. Therefore, the examination is made in terms of the amount of data representing the additional information. For modeling, it is worth calling the general energy model for help[9]. The general energy model is based on philosophical foundations. It adapts the abstract categories of human thinking. These categories are Object, Property, and Relationship. The energy equivalents of these are Transformation, Storage and Transmission. The system model is accordingly based on three types of basic elements. The energy balance shows that some of the energy flowing into the system from the outside is stored and the rest is radiated out of the system. Meanwhile, the energy can be transformed[9]. The general model is shown in Figure 2.
ENERGY IMPORTANCE
To explore the energy problems, it is worth starting from the energy balance formula (1) of the aforementioned system model.The formula (2) corresponding to the other initial condition is the energy demand formula, which expresses the amount of required and added energy.
E(in) = delta E(store) + E(out), (1)
E(all) = E(need) + E (add). (2)
Since the two formulas represent independent test aspects, the simple (3) and elaborated form of the formula derived from the matrix of the two formulas can also be given (4).
E(in/all/) = delta E(store/all/) + E(out/all/), (3)
E(in/need/) + E(in/add/) = delta E(store/need/) + delta E(store/add/) + E(out/need/) + E(out/add/). (4)
Formula (4) can be decomposed into two equations: to a formula representing the aspect of the energy required (5), and to a formula representing the added energy (6).
E(in/need/) = delta E(store/need/) + E(out/need/), (5)
E(in/add/) = delta E(store/add/) + E(out/add/). (6)
The identical form of formulas (1) (5) and (6) shows that the energy problems in the handling of additional information can be included in the same system of aspects as in the case of general information handling problems. This is a logical conclusion, since the abstraction of information takes place through the interpretation of data. Accordingly, the additional information must be stored, so it binds excessive processing capacity, and it requires additional bandwidth.
SUMMARY
In order to implement the smart city concept[25][26][27][28][29], it is essential that its implementation is based on a high-availability, long-term, sustainable, and reliable infocommunication infrastructure[1][2]. The main purposes of infocommunication systems are data storage, processing and transmission[1]. During data transmission, more data is transferred than is required. This is not just due to intentional redundancy.When transferring media materials, a much larger amount of extra data is added to the data representing the useful information. The present study has shown, through the example of an online game, that a considerable amount of extra data can be transferred due to the possible negligence from the part of the tax side of the data transfer[23].The receiving side can interpret the data in several ways, so this data can contain additional information. In published data streams, the decoding of this additional information is a form of information acquisition (OSINT) that is part of the technical palette of social engineering[24]. Furthermore, the study has shown, using the energy modeling of systems, that the additional information has the same energy problems as useful information. Accordingly, the additional information must be stored, an additional processing capacity and extra bandwidth is required. This need must be taken into account when designing systems. Given that much of the amount of the data generated is a media stream in which significant extra data is present, the additional information also plays a significant role in the rapid increase in the energy demand of systems, as well as in the big data effect.