INTRODUCTION
In this article, the information technology (IT) approach to city/building constructions, and the construction of interconnecting systems have been discussed. Their significance is due to the fact that as early as the planning stage, a large amount of data (such as personal data, technical designs, financial documents, etc.) will be collected and managed, and they will be classified as confidential or even secret. It should be taken into consideration that there are several buildings, objects, or things in which some type of a sensor is installed, and in some way they communicate the state of the systems or even the measured readings to the user. If this information is accessible to an unauthorized person, it can be misused, which will cause damage. Two important facts can be deduced from the above information. The first is that nowadays it is increasingly difficult to mention anything that is not controlled by electronics or is not networked, which means that nearly everything communicates with the system user. The other fact is that as early as at the planning phase – that is well before any physical work is done on the construction site – significant risks can be expected[1].
EXAMINATION OF CONSTRUCTION PROJECTS
Sensitive information at risk (including later phases of the construction process) may include: (Day-to-day) organization plan (nature of workflows, workflow areas, company manpower, expected material deliveries, temporary and permanent storage areas, type and quantity of equipment and materials in warehouses and construction sites); construction plan of the structure of buildings; network and system blueprints for buildings (electrical network, water and sewage network, gas pipeline network, IT network, security system network, fire alarm network,); details of general contractor; regulations of the general contractor and those of the operation of the construction site; details of subcontracting companies; partnership contracts and commitments; performance confirmations and payments; official approvals; events and event logs; etc.[2][3]. Data management may vary significantly from country to country. In the case of China, information gathering is centrally managed. Based on the data collected from different systems, the rights of the population are determined or even limited. When it comes to the European Union, it is the legal harmonization between the EU member states that plays an important role. Its objective is to develop and adopt regulations among the parties, which do not violate each other’s rights. In recent years perhaps the best example of this effort has been “Regulation (EU) 2016/679 of the European Parliament and of the Council of 27 April 2016 on the protection of natural persons with regard to the processing of personal data and on the free movement of such data, and repealing Directive 95/46/EC (General Data Protection Regulation)”, referred to briefly as the GDPR. Of the latter, it should be noted that it applies only to personal data, while it is not applicable to company secrets or confidential data[4]. Data and the networks that transfer them are omnipresent, and therefore, inevitable. The question is how these values can be protected. The answer is given through a complex system. Basically, there are three main categories of data carriers[5][6]: Persons as data carriers: A knowledge-based factor that may be intentionally or accidentally compromised. Hard copy (and traditional) media: This type includes various administrative tasks, treatment of documents and its entire process. IT-based media: The management of IT systems, including their operation, user management.
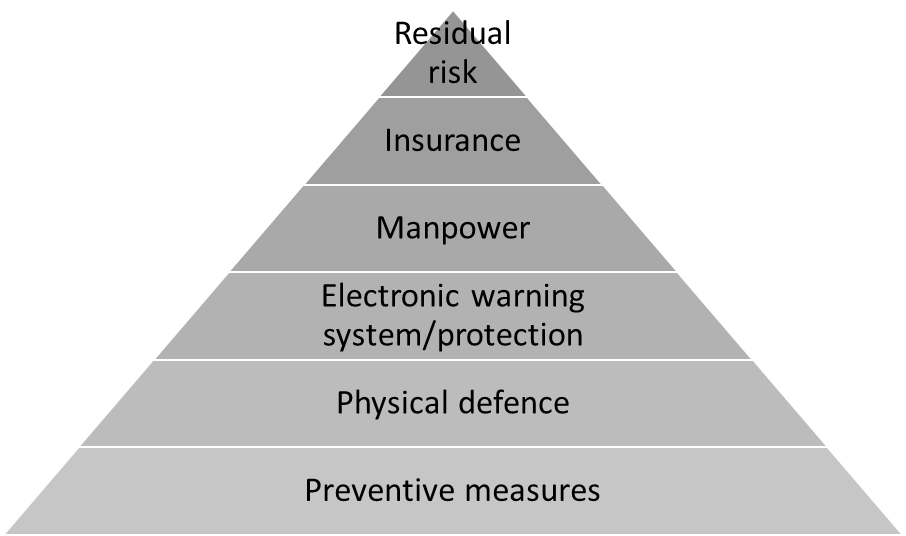
The security pyramid provides a well-structured, general guidance. The security pyramid illustrates the components of protection and how they are built on one another. Each level has its own “mission”[8][9][10][11][12]. Each level can be further divided into sub-levels or components which may be called efficient, in dependence on having met the criteria. The summary of its levels (with reference to building protection): The lowest level is made up by preventive measures. Basically, this is the fundament of the entire system, which is present anywhere at other levels as well. These measures include the introduction of and compliance with regulations and measures, without which other levels would be ineffective. For example: If the front door of a house is not closed, the physical protection built into the door, which is the lock in this case, will not serve its purpose. If the intrusion detection system is not armed, it will not signal the intruder. The level of physical protection2 consists of physical devices that make it difficult to enter or exit a given facility (e.g. a prison). Applying the previous example: If the door of a house is closed, but no built-in lock is available, no protection can be ensured in spite of any intention to protect the building. The level of electronic signalling systems is responsible for signalling intrusions. The function of various different sensors – movement, opening, breaking, vibration, sound etc. – is to signal in cases other than the “normal” (event-free) status. An electronic version of protection is an electronic device which is able to resist an intrusion regardless of its effect. The front door of a house has a lock and it is locked. If there is nothing to signal the alteration of normal status – e.g. in the case of a break-in, which is considered as a deviation from a “normal” status, that is the closed position –no protection will be provided. The level of personnel is responsible for the immediate elimination of perceived adverse acts. This category includes the human force responsible for protection (bodyguards, security personnel, armed security guards, K-9 guards – the police in some respects – and trained (guard)dogs). The front door of a house has a lock and it is locked. If the intrusion detection system signals but there is no one to respond to the intrusion alarm, the necessary protection will not be achieved. In spite of the security measures taken and established, a harmful event may occur in an unpredictable manner (for example, the attacker somehow gains access to the secured object, the fire extinguisher does not put out the fire, or not in the expected way, etc.), which may even be a chain of accidental events. In such cases it is the insurance service that will compensate the injured party. The top level of the pyramid is represented by the so-called residual risk factors (also known as own risks). This level is always present, but its value or magnitude can be influenced. The more hazards are eliminated / minimized or the closer the probability of their occurrence is to zero, the lower its indicated value is. Since one cannot prepare for everything, this value can never equal zero. There may also be a model similar to the security pyramid, which for simplicity will now be labelled as “extended security pyramid”.
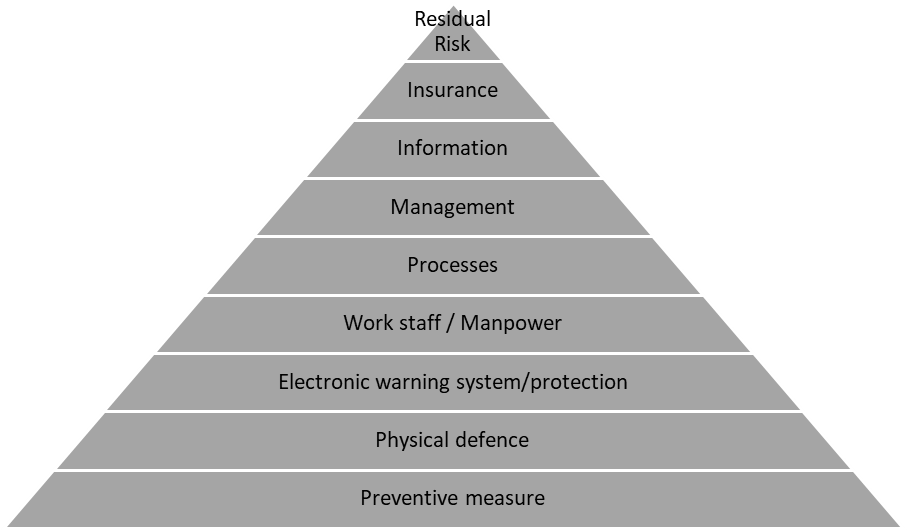
The extended security pyramid has another three levels added: processes, management, information, and at the level of labour force, the staff also appeares. A significant part of an organization is made up by employees who are not part of the security personnel. Through their involvement and security training, security risks can be reduced. Well-trained staff will initially be passive but later on, they get dynamically involved in security activities. Passive participation means simple compliance with the rules and regulations, while active involvement means noticing vulnerability or attack activities, and taking some action against them (signalling to security, recognising suspicious activities, etc.). “Information” represents a significant part, as it comprises the basis of the decision-making process at management level. Various processes and their orders of execution are determined on the basis of information. These processes can be considered as the instructions of the organization. The composition of the instructions consists of the relevant legislation and the internal, individual regulations of the organization. These regulations include, for example, the rules of the operation of the organization or organizational unit, the various organizational and production processes, or even the rights and obligations of guarding and security. For those with no or limited security awareness the extended security pyramid gives a greater insight into how the system of the company works. In contrast, the other security pyramid consisting of fewer levels tends to be based on its main pillars, helping to make the levels more transparent and easier to memorise. Unlisted levels are included in various standards, and partly in legislation, each of which is integrated into different levels. There are several examples to prove the above statements through asking and answering the following questions: Can a deal be concluded between a seller and a buyer if either of them is not aware of the other, or possibly of the product to be sold? Obviously not, because there is a lack of information and of its flow. The seller and the buyer can make a decision to sell or buy a product based on the necessary information. At this level (personal) management appears. What is the process of sale and purchase? The rules of the process (rules of procedure) are determined by the legislation and the participating parties. This is where the level of process appears. The security pyramid (including the extended one) formulates levels that can be interpreted and applied as a system in other branches of security technology as well. Returning to the original question of how values and valuables can be protected, the answer lies in the security pyramid shown above, that is, in the regulation and technology of its elements.
CONCLUSION
In the course of construction work, a large amount of data and information is transferred, most of which is classified as personal or confidential. If these data are not handled with due care, they can be compromised and easily misused. The article briefly summarizes what data could be involved and how it could be carried. Examining the above possibilities, it can be claimed that the key to the problem is the relationship between the security pyramids, the elements of the pyramid and their regulation.
REMARKS
1On the basis of other approaches, the structure of a pyramid or its levels would not be possible to interpret. E.g., 1) from an economic aspect, the budget of used solutions may significantly differ depending on the facility to protect, which means that the lowest level of the pyramid would not be made up by preventive measures. 2) in the interpretation of protective solutions, residual risk could not be interpreted. Through insurance, which is optional, it is only the extent of the harmful event that may be decreased, while the residual risk would not be involved in risk reduction. Nevertheless, this approach is applied here, because it can be interpreted as a general thumb rule, as a “technically” structured system. 2Mechanical protection may be a more precise term. the two terms are used here as synonyms.